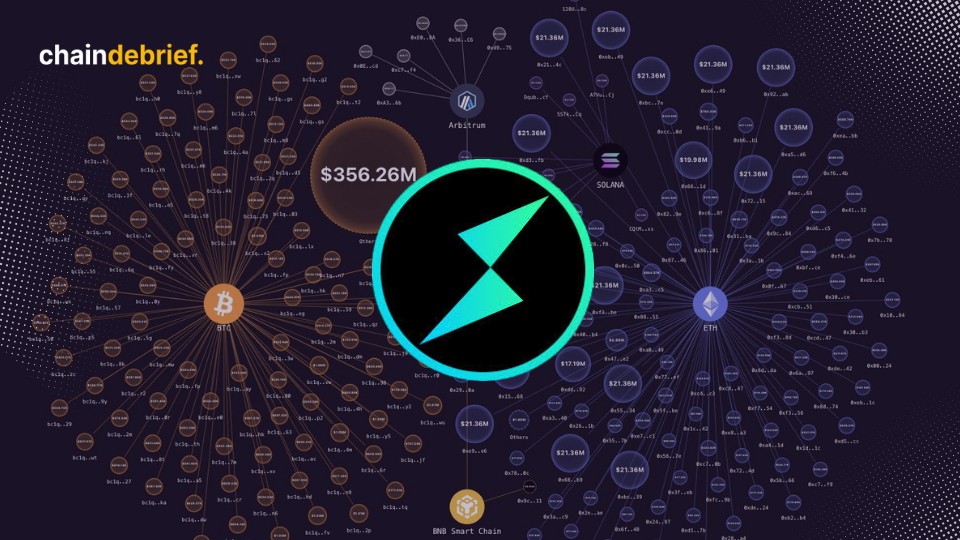
On March 4, 2025, Bybit CEO Ben Zhou confirmed that $1.07 billion of the stolen assets from the recent $1.4 billion breach could still be traced. The hack occurred on February 21, 2025, when hackers managed to steal over 499,000 ETH along with other tokens.
3.4.25 Executive Summary on Hacked Funds:
— Ben Zhou (@benbybit) March 4, 2025
Total hacked funds of USD 1.4bn around 500k ETH, 77% are still traceable, 20% has gone dark, 3% have been frozen.
Breakdown:
– 83% (417,348 ETH, ~$1B) have been converted into BTC with 6,954 wallets (Average 1.71 btc each) . This and…
Most of these stolen funds were quickly laundered using THORChain, a decentralized platform designed for cross-chain asset swaps. While a portion of the funds has been successfully tracked, much of it remains hidden due to the sophisticated methods the hackers used to cover their tracks.
The swift laundering process demonstrates how decentralized platforms can be exploited for criminal activities. In this case, THORChain, which allows seamless transactions between different blockchains, became a crucial tool for the hackers to move the stolen assets.
The decentralized nature of THORChain made it difficult for authorities to halt the laundering process in real time, further complicating efforts to recover the stolen funds.
You can also read this Bybit Fully Replaces Stolen $ETH After $1.4B Hack
THORChain’s Role in Facilitating the Laundering
THORChain played a central role in the hackers’ laundering operations. According to Bybit, the attackers converted approximately 83% of the stolen assets—around 417,348 ETH—into Bitcoin (BTC). They then spread the funds across 6,954 wallets, which made tracking and recovery significantly more difficult.
The surge in transaction volume on THORChain following the hack, which reached over $5.8 billion, raised red flags about the platform’s involvement in facilitating these illicit activities.
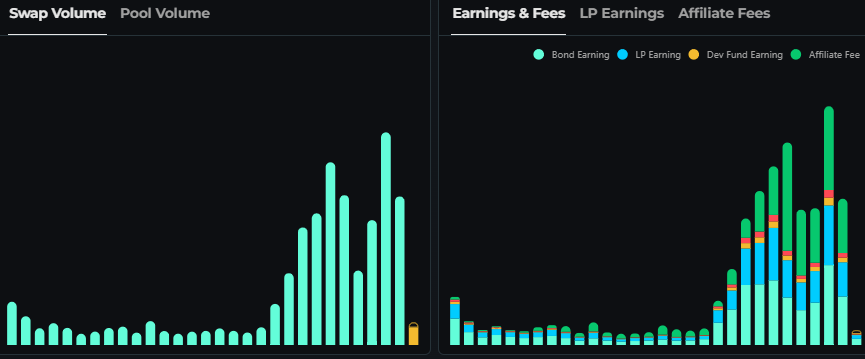
Critics of THORChain’s system, including blockchain security expert Taylor Monahan, argue that the platform’s decentralized nature allows it to operate within a “bubble” that inadvertently enables money laundering.
This isolated ecosystem benefits insiders and criminals who find ways to exploit the system for illicit gains. The incident has sparked a wider debate about the need for tighter regulations and security measures within decentralized finance (DeFi) platforms.
Efforts to Freeze and Recover Stolen Funds
Despite the hackers’ attempts to cover their tracks, Bybit’s investigation into the breach has led to some recovery of stolen assets. Zhou reported that $42 million of the stolen funds had been successfully frozen. Additionally, 11 independent bounty hunters received a total of $2.1 million in rewards for their role in helping track down and freeze assets.
Platforms like Mantle, Paraswap, and blockchain expert ZachXBT have contributed significantly to this effort, but much of the stolen funds remain unaccounted for due to the complexity of the laundering methods.
This situation has shown that, despite improvements in blockchain analytics and tracking technology, the nature of DeFi platforms presents significant risks for asset security.
You can also read this Trump to Host Historic White House Crypto Summit on March 7
The Implications for Crypto Security and Industry Response
The Bybit hack underscores the critical need for stronger security protocols in the cryptocurrency industry, particularly within decentralized platforms. Experts suggest that solutions like off-chain transaction validation could help mitigate similar breaches in the future.
By improving security measures and fostering better collaboration between crypto firms, regulators, and cybersecurity professionals, the industry can better protect itself from increasingly sophisticated attacks.
Bybit’s quick response to freeze the stolen funds and launch recovery efforts highlights the importance of proactive security measures. However, as decentralized finance continues to grow, platforms like THORChain will need to implement more robust security features to prevent such breaches.
[Editor’s Note: This article does not represent financial advice. Please do your own research before investing.]
You can also read this You can also read this Trump to Host Historic White House Crypto Summit on March 7